Purview DLP in SharePoint and OneDrive External Sharing: How It Works
Data Loss Prevention (DLP) in Microsoft 365 plays a critical role in safeguarding sensitive data within SharePoint and OneDrive. One of the key aspects of DLP is its behaviour when files are shared externally. This blog post explores how Purview DLP in SharePoint and OneDrive External Sharing reacts when files are shared with external users, when actions trigger, and the impact of proactive blocking.
This blog post was written in response to a query from a former customer, and it took considerable testing to understand the nuances of DLP behavior. I had once seen DLP automatically blocking files from external user access the moment they were uploaded, and the conditions were satisfied. Little did I know that it depends on what action you configure.
DLP Policy Configuration and Rules
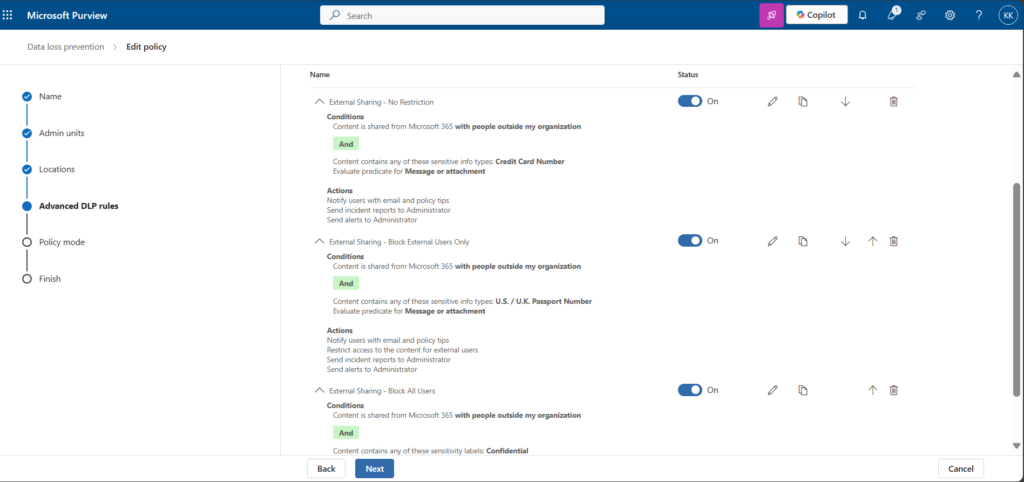
To test DLP behavior, I configured a policy targeted to SharePoint and OneDrive, covering one SharePoint site and one OneDrive location. The policy included the following three rules:
| Rule | Conditions | Actions |
|---|---|---|
| Rule 1: External Sharing – No Restriction | – Content is shared from Microsoft 365 with people outside my organization – Content contains any of these sensitive info types: Credit Card Number | – Notify users with email and policy tips – Send incident reports to Administrator – Send alerts to Administrator |
| Rule 2: External Sharing – Block External Users Only | – Content is shared from Microsoft 365 with people outside my organization – Content contains any of these sensitive info types: U.S. / U.K. Passport Number | – Notify users with email and policy tips – Restrict access to the content for external users – Send incident reports to Administrator – Send alerts to Administrator |
| Rule 3: External Sharing – Block All Users | – Content is shared from Microsoft 365 with people outside my organization – Content contains any of these sensitivity labels: Confidential | – Notify users with email and policy tips – Restrict access to the content – Send incident reports to Administrator – Send alerts to Administrator |
Observations from Testing
To analyze DLP behavior, I uploaded documents matching all three rules to a SharePoint site where an external Gmail user was already added as a member of the site. Here’s what happened:
Key Findings:
-
DLP does not trigger when an external user is added at the site level.
-
The external user had access to the SharePoint site, but DLP did not restrict access at this stage.
-
This confirms that DLP policies only apply at the file-sharing level, not when an external user is simply part of a SharePoint group.
-
-
Blocking External Users Only rule proactively blocked external access upon upload.
-
When I uploaded a document containing a U.K. Passport Number, this rule triggered immediately and blocked external access.
-
This was significant because the file had not yet been explicitly shared—DLP still enforced the block.
-
The external user who was already a site member could not access the file despite their prior site-level permissions.
-
Now one would assume that the DLP policy triggered immediately because of the external user present but that is not the case. I had tried the same thing with OneDrive where no external user was present, but the policy did trigger and still blocked the file. This is called Proactive Blocking.
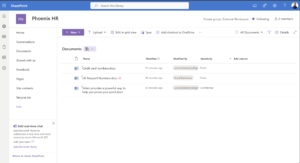
Rule 1 & 3 not enforced. Rule 2 proactively blocks the file.
-
-
No Restriction and Block All Users rules only triggered when files were explicitly shared.
-
The file containing a Credit Card Number (No Restriction rule) was not blocked immediately.
-
The file labeled Confidential (Block All Users rule) was not blocked immediately.
-
Only when these files were explicitly shared with an external user did DLP take action.
-
-
Site-level external membership does not override DLP policies, well it depends.
-
Even though an external user was added to a SharePoint group, they could not access a file proactively blocked by the Blocking External Users Only rule.
-
This ensures that sensitive files remain protected regardless of broader site permissions.
-
-
Immediate blocking is only possible with the Blocking External Users Only rule.
-
If an organization needs an instant restriction on external access, this rule must be configured.
-
Other rules depend on explicit file sharing before triggering.
-
-
Incident reports and alerts provide visibility.
-
No alerts or incident reports were generated, but the “DLP rule match” was visible in the Activity Explorer for Blocking External Users Only rule.
-
Incidents and Alerts were reported for the other rules.
-
-
DLP configurations must align with business needs.
-
Not all organizations may need immediate blocking.
-
However, knowing how DLP behaves helps admins implement policies effectively.
-
Why This Matters
This finding is important because many assume that adding external users at the site level will automatically enforce DLP controls. However, only Rule 2 proactively restricts external access upon upload, even before sharing occurs. This means organizations that want to ensure immediate blocking of sensitive files from external access should configure a “Block External Users Only” rule in their DLP policies.
“Action Not Configured” and “Block Everyone” don’t fire proactively and can’t prevent external users from accessing the file, rendering them ineffective if you have external users at the site level.
Best Practices for Configuring DLP Policies
- If your goal is strict external access control, include Rule 2 to enforce restrictions immediately upon file upload.
- Do not rely on site-level external user restrictions—DLP policies only apply at the file-sharing level.
- Use incident reports and alerts to monitor sharing activities and ensure compliance.
Conclusion
The key takeaway is that DLP does not trigger simply because an external user is added at the site level—file sharing actions dictate enforcement. However, a properly configured “Block Externals Only” rule ensures that external users cannot access sensitive files, even if they are site members.
By strategically configuring Purview DLP in SharePoint and OneDrive External Sharing, organizations can better protect their sensitive data from unintended external exposure.
Have you encountered similar challenges with DLP in SharePoint and OneDrive? Share your experiences in the comments!




